Overview
This page acts as an overview of organization’s attack surface with overall detections:
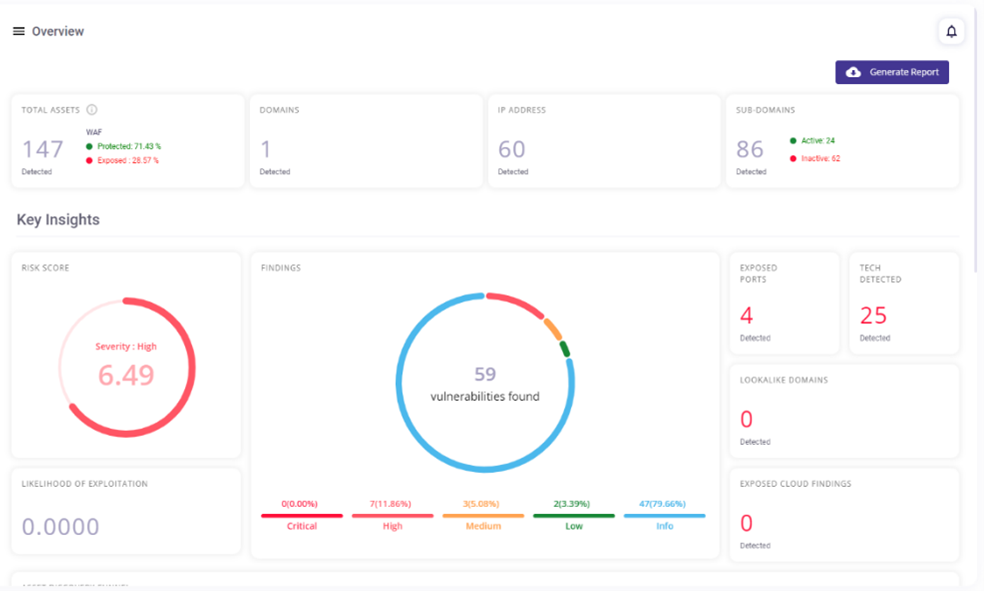
Total assets consisting of:
- Domains
- Subdomains (along with pulse analysis active-inactive)
- IPs
- WAF Protected to Exposed insights for each asset.
Key Insights like:
- Risk Score: A comprehensive metric quantifying the collective risk exposure of an organization.
- Likelihood of Exploitation: Indicates the probability that a system vulnerability will be successfully targeted and exploited by an attacker.
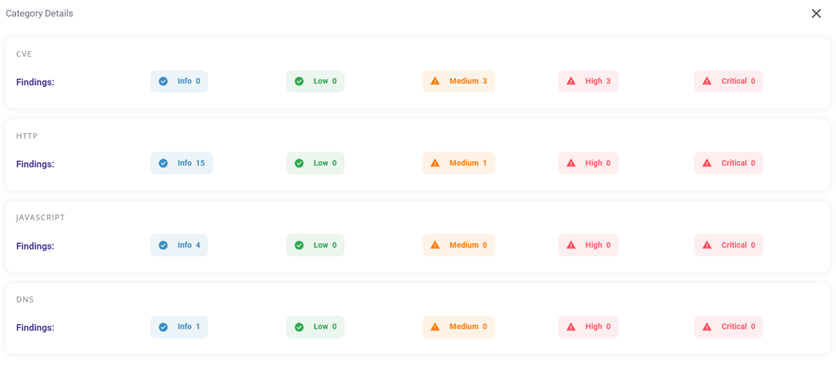
- Findings: Shows the count and percentage of vulnerabilities, categorized by severity levels including informational, low, medium, high, and critical.
- Exposed Ports: Accessible ports on servers or systems, exposing services to the internet.
- Tech Stack: Technologies identified on domains or subdomains, including outdated software versions.
- Lookalike Domains: Domains closely resembling legitimate ones, posing a potential phishing risk.
- Exposed Cloud Findings: Instances where cloud storage buckets are inadvertently accessible, potentially exposing sensitive data (confidential files, reports and more).
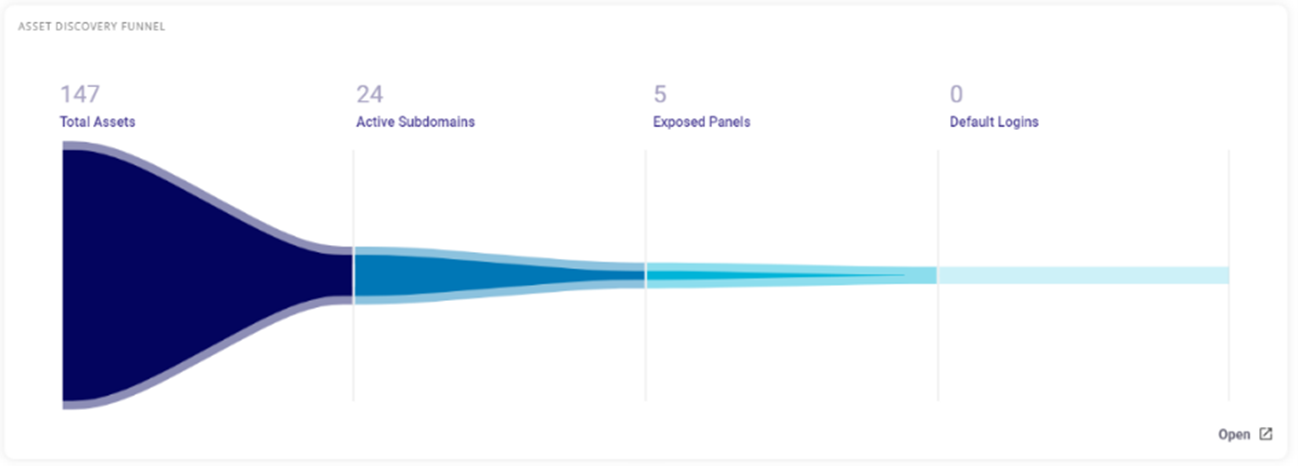
- Assets Discovery Funnel: The Asset Discovery Funnel offers a risk prioritization approach by filtering assets through a series of stages: from total assets to active subdomains, to exposed panels, and finally to default logins.
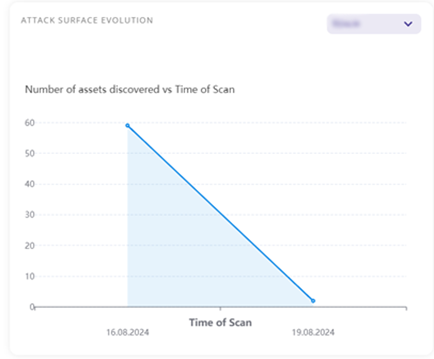
- Attack Surface Evolution: Tracks changes in your organization's attack surface over time, identifying areas for reduction and providing asset count trends.
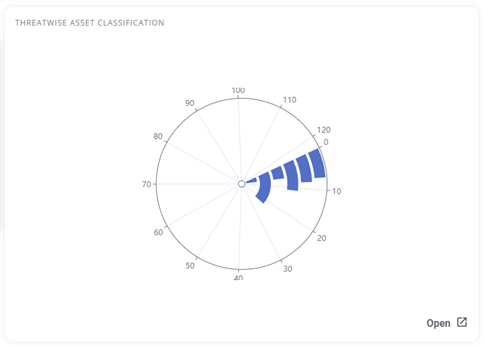
- Threat Wise Asset Classification: Classification of assets based on clustered threats, aiding in risk prioritization and remediation measures.