Palo Alto Cortex XDR Integrations
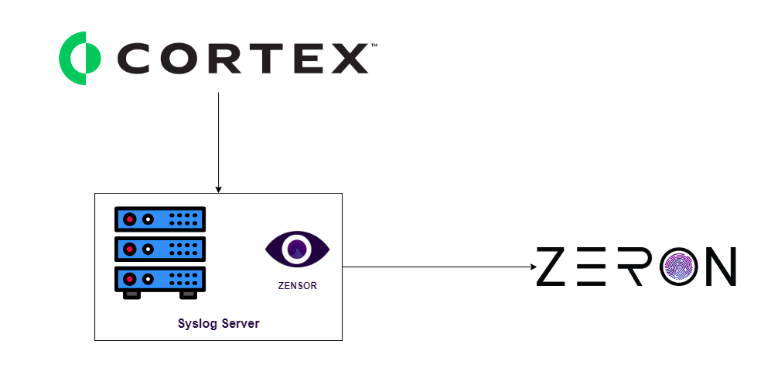
Methodology: Syslog
Process: Barracuda email protection Syslog logs will be exported to a Syslog server. From that Syslog server, logs will be transferred to Zeron via Zensor.
To send Cortex XDR notifications to your Syslog server, you need to define the settings for the Syslog receiver from which you want to send notifications.
Before you define the Syslog settings, enable access to the following Cortex XDR IP addresses for your deployment region in your firewall configurations:
REGION LOG FORWARDING IP ADDRESSES United States - Americas (US) - 35.232.87.9
- 35.224.66.220Germany (DE) - 35.234.95.96
- 35.246.192.146Netherlands - Europe (EU) - 34.90.202.186
- 34.90.105.250Canada (CA) - 35.203.54.204
- 35.203.52.255United Kingdom (UK) - 34.105.227.105
- 34.105.149.197Singapore (SG) - 35.240.192.37
- 34.87.125.227Japan (JP) - 34.84.88.183
- 35.243.76.189Australia (AU) -35.189.38.167
- 34.87.219.39United States - Government - 104.198.222.185 India (IN) - 34.93.247.41
- 34.93.183.131Switzerland (CH) - 34.65.228.95
- 34.65.74.83
Select Settings → Configurations → Integrations → External Applications.
In Syslog Servers, add a + New Server.
Define the Syslog server parameters:
Name—Unique name for the server profile.
Destination—IP address or fully qualified domain name (FQDN) of the Syslog server.
Port—The port number on which to send Syslog messages.
Facility—Choose one of the Syslog standard values. The value maps to how your Syslog server uses the facility field to manage messages. For details on the facility field, see RFC 5424.
Protocol—Select a method of communication with the Syslog server:
TCP—No validation is made on the connection with the Syslog server. However, if an error occurred with the domain used to make the connection, the Test connection will fail.
UDP—Cortex XDR runs a validation to ensure connection was made with the syslog server.
TCP + SSL—Cortex XDR validates the syslog server certificate and uses the certificate signature and public key to encrypt the data sent over the connection.
Certificate—The communication between Cortex XDR and the Syslog destination can use TLS. In this case, upon connection, Cortex XDR validates that the Syslog receiver has a certificate signed by either a trusted root CA or a self-signed certificate. You may need to merge the Root and Intermediate certificate if you receive a certificate error when using a public certificate. Up to TLS 1.2 is supported.
If your Syslog receiver uses a self-signed CA, Browse and upload your self-signed Syslog receiver CA.
Make sure the self-signed CA includes your public key. If you only use a trusted root CA leave the Certificate field empty.Ignore Certificate Error—Cortex XDR does not recommend, but you can choose to select this option to ignore certificate errors if they occur. This will forward alerts and logs even if the certificate contains errors.
Test the parameters to ensure a valid connection and create when ready. You can define up to five Syslog servers. Upon success, the table displays the Syslog servers and their status.
(Optional) Manage your Syslog server connection. In the Syslog Servers table
- Locate your Syslog server and right-click to Send text message to test the connection.
Cortex XDR sends a message to the defined Syslog server which you can check to see if the test message indeed arrived.
If the message doesn’t arrive, Cortex XDR displays an error. View the error details and suggested solutions in Syslog Server Test Message Errors. - Locate the Status field.
The Status field displays a Valid or Invalid TCP connection. Cortex XDR tests connection with the Syslog server every 10min.