Asset Details
Please click on the Pencil Icon located next to your system.
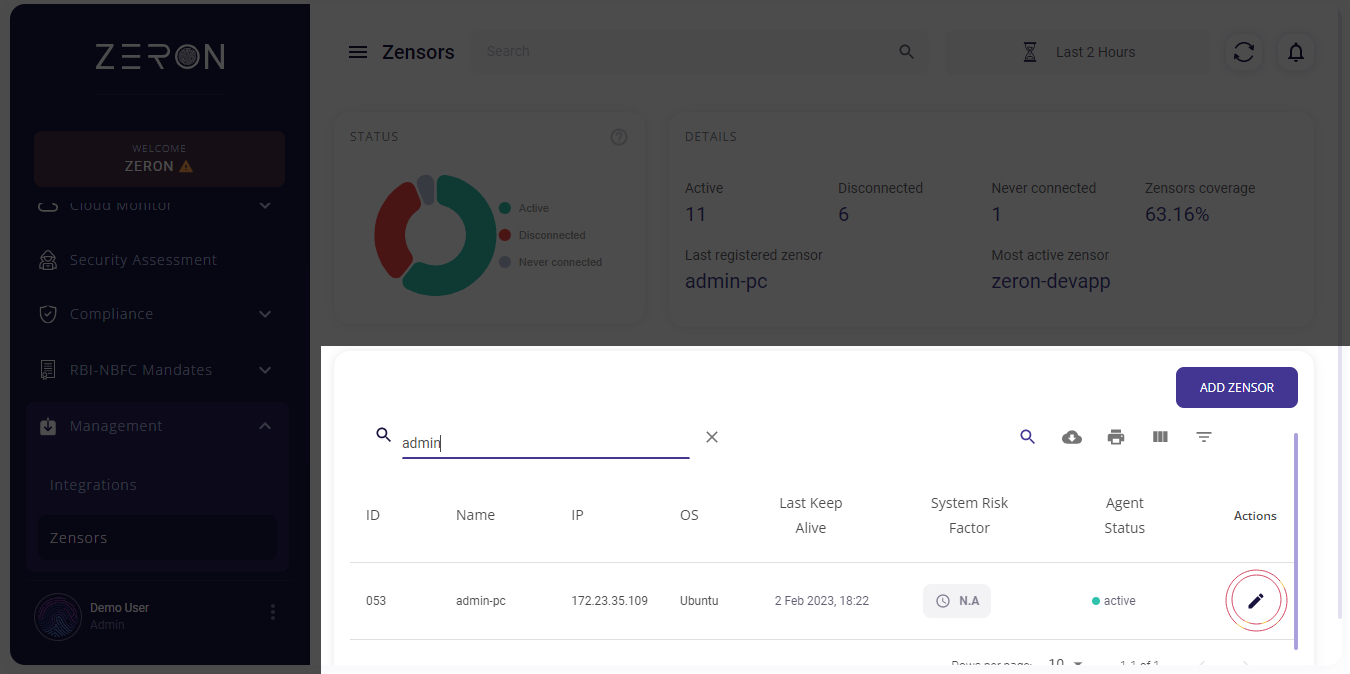
An asset details edit form will pop-up
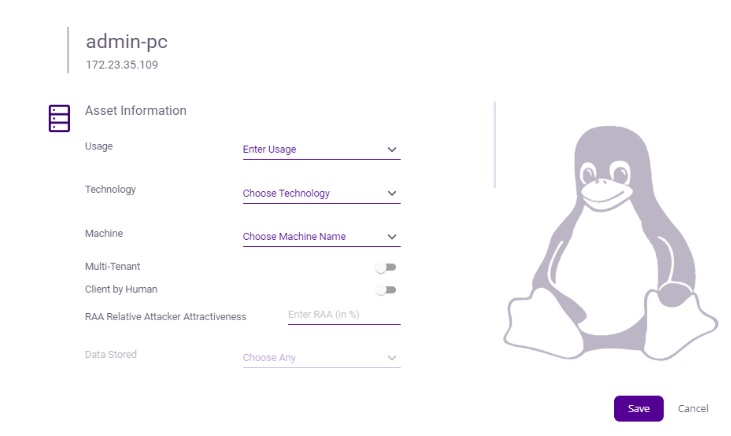
Asset Information
Usage: What is the system intended to be used for; Automation, Business or Storage?
Technology: What type of technology is utilized for activities such as testing Enterprise Resource Planning (ERP) systems or databases?
Machine: Is the machine physical or virtual?
Multi-Tenant: If there are multiple user accounts present in the machine, kindly click the toggle button to proceed.
Client by Human: If utilized by a human, please activate the toggle button.
RAA Relative Attacker Attractiveness: For each technical asset the Relative Attacker Attractiveness (RAA) value was calculated in percent. The higher the RAA, the more interesting it is for an attacker to compromise the asset.
Data Stored: What kind of data is held in this system? Is it client PII (Personal Identifiable Information) data or API keys?
Data Processed: What kind of data is being processed within that system? Is it client PII (Personal Identifiable Information) data or operational data?
Asset Rating
Confidentiality: Degree of Confidentiality: Public/Private.
Integrity: The level of integrity is essential/low.
Availability: The level of availability is imperative/low.
Business Impact
Traffic Light Protocol: The level of disruption to business operations if the system is breached.
Database Contained
Traffic Light Protocol: The level of damage that could be caused to the system database if a security breach were to occur.
Criticality
Domain wise system criticality choose any one.