Subdomains and IP Addresses
This section displays all the subdomains and IPs that have been detected for the chosen target.
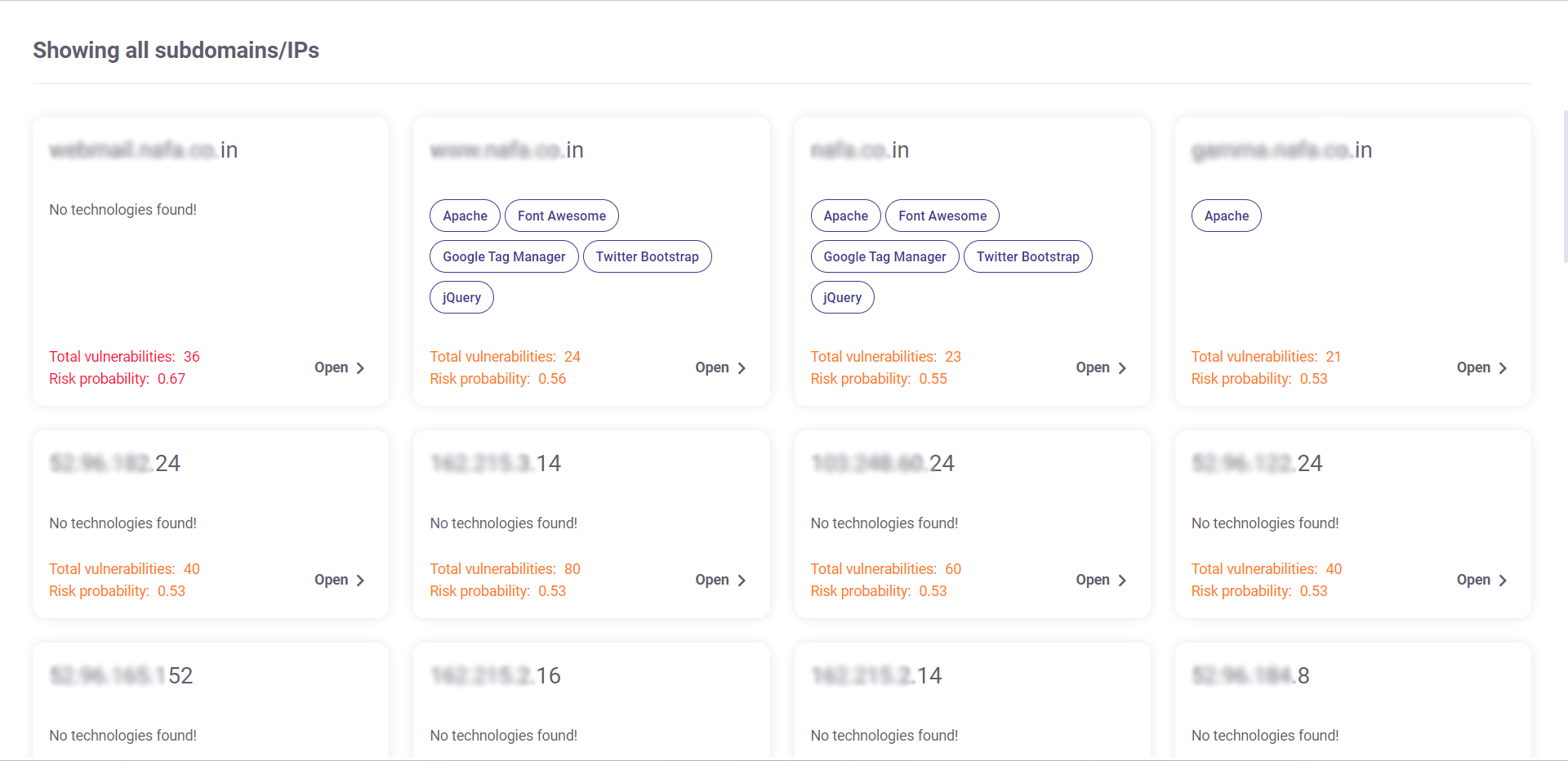
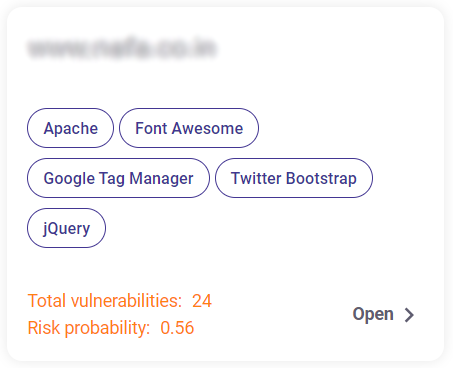
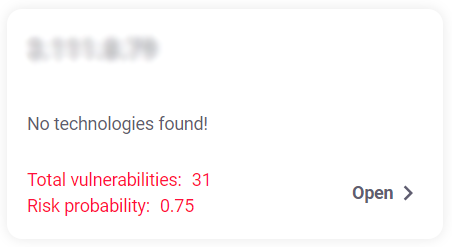
Each tile in this section provides an overview of the subdomain and IP addresses by displaying the following info:
- Name of the subdomain/ IP address
- Technologies found
- Total vulnerabilities
- Risk probability
Subdomains
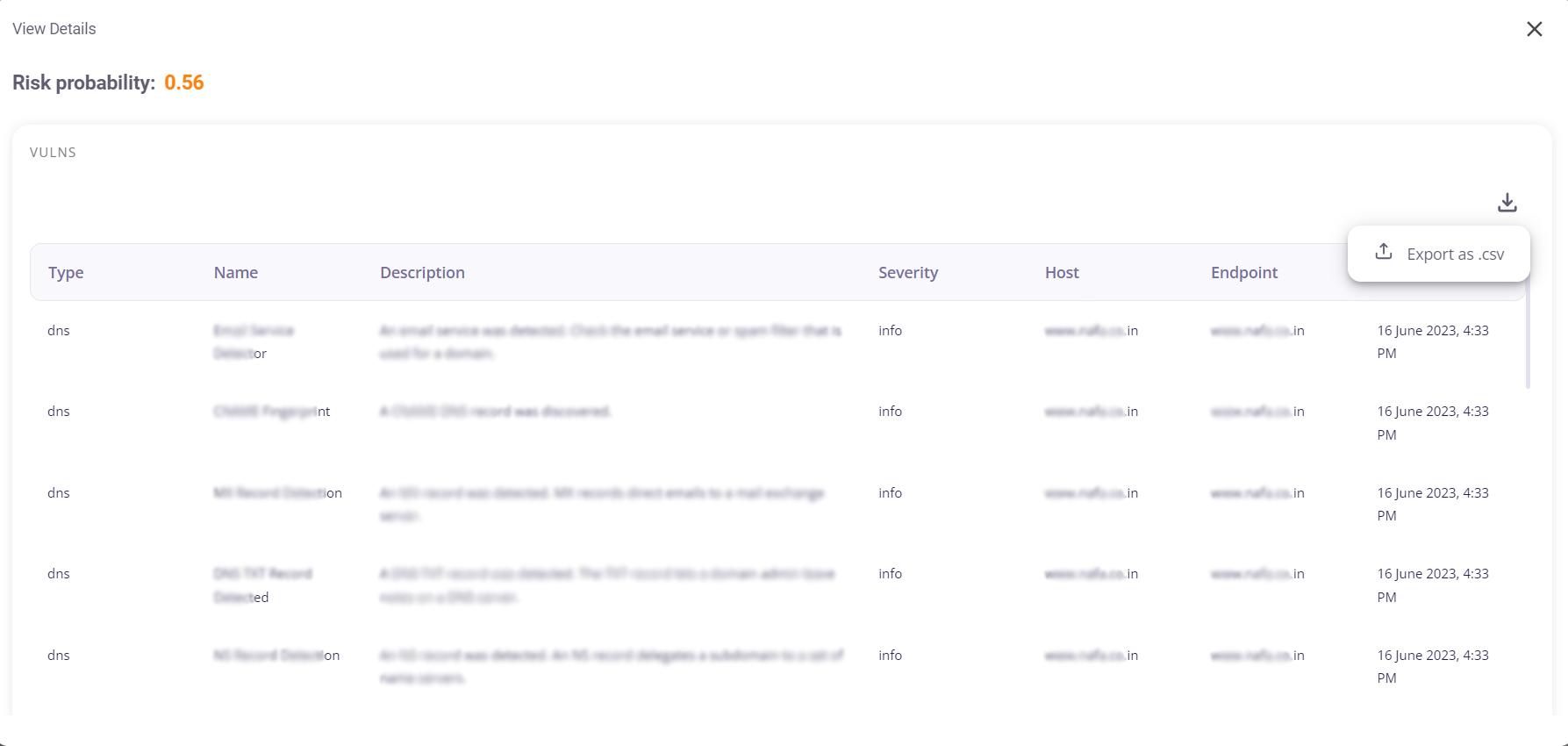
Clicking on the 'Open' button on a Subdomain tile would provide the user with the following details about the vulnerabilities, in a tabular format:
- Risk probability
- Type of vulnerability
- Name
- Description
- Severity
- Host
- Endpoint
- Timestamp.
The severity of the risks is based on the below colour code:
- High
- Medium
- Low
Risk probability
Risk probability
Risk probability
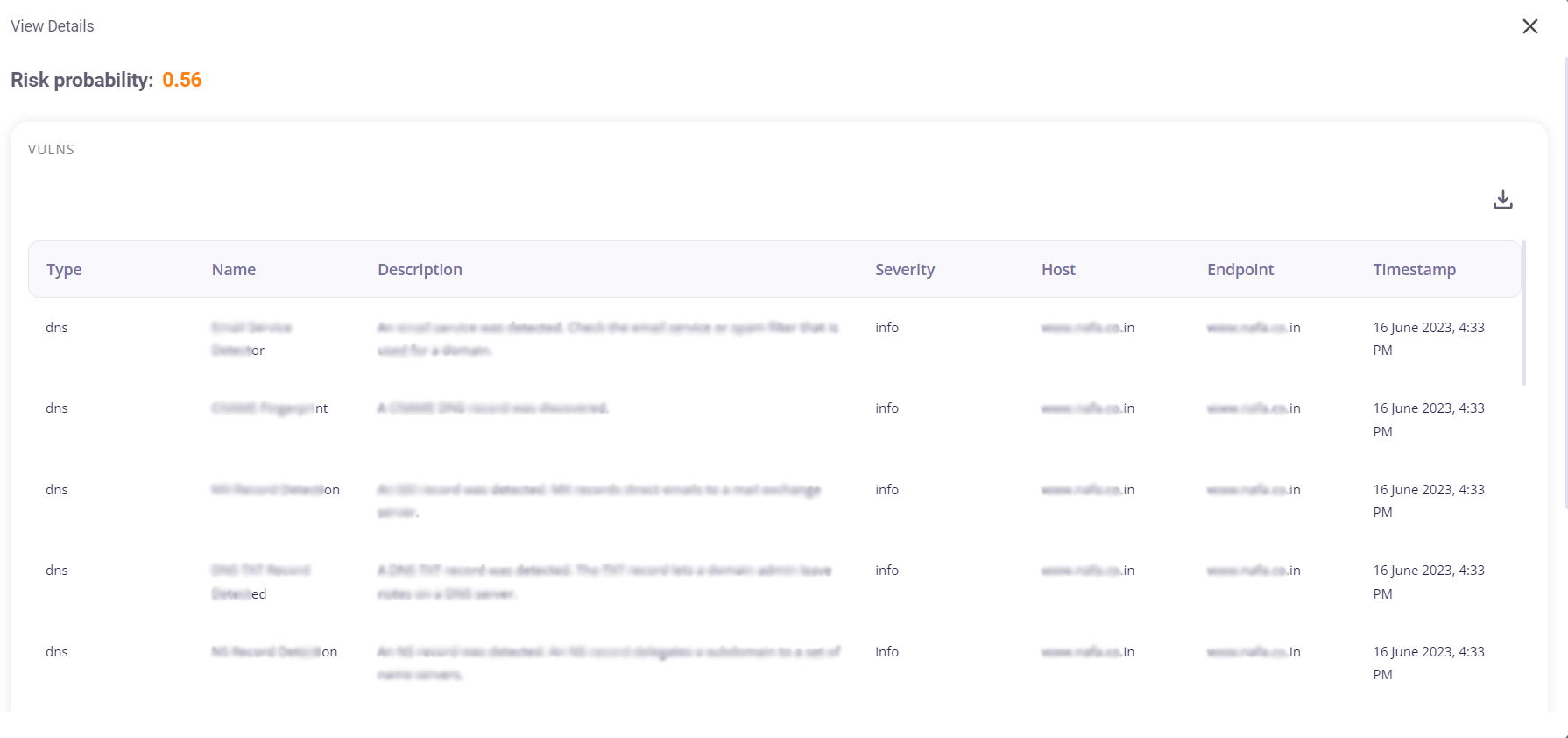
This tabular info can be downloaded as a .csv file by clicking on the download button at the top right corner.
IP addresses
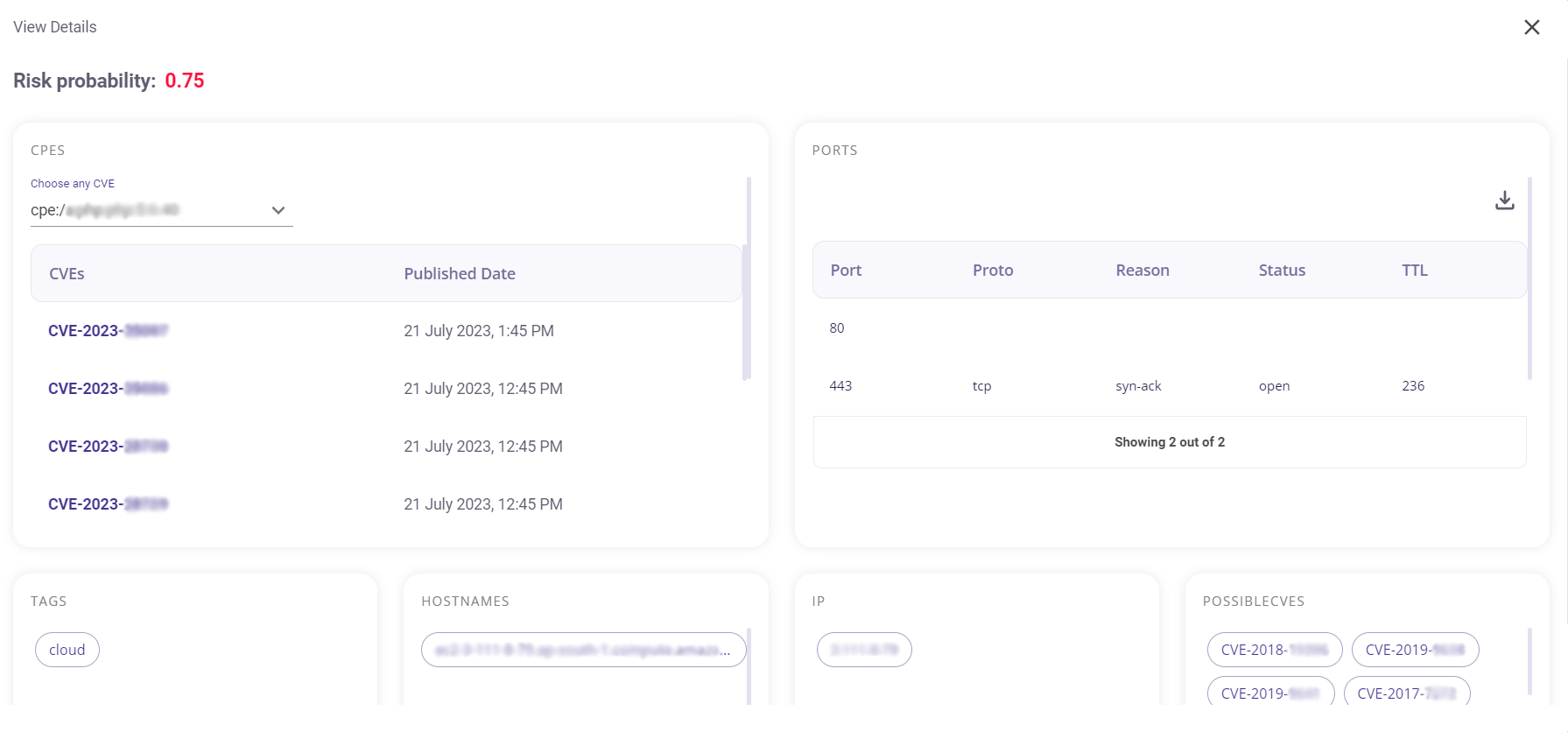
Clicking on the 'Open' button on an IP address tile would provide the user with the following details about the vulnerabilities:
- Risk probability
- CVEs (for each CPE)
- Open ports
- Tags
- Hostnames
- IP address
- Possible CVEs
The severity of the risks is based on the below colour code:
- High
- Medium
- Low
Risk probability
Risk probability
Risk probability
| Aspect | CPES (Common Platform Enumeration) | CVEs (Common Vulnerabilities and Exposures) |
|---|---|---|
| Description | focuses on system configurations, detailing the setup and components of hardware and software. | specific identifiers assigned to vulnerabilities in software systems. These IDs are used to discuss and track security issues. |
| Example | Example CPES: cpe:/o:microsoft:windows:10 | Example CVE: CVE-2023-12345 |
| Focus | emphasizes identifying different system components and their versions. | highlight individual vulnerabilities within software systems, pinpointing security risks. |
| Use Case | used to determine affected systems based on configurations. | employed to reference and discuss vulnerabilities, enabling security conversations. |
| Link to Issues | associated with configuration data, aiding in assessing system setup. | directly linked to detailed information about vulnerabilities, assisting in risk assessment. |
| Mitigation Usage | helps identify impacted systems, allowing for targeted security measures. | provide information about specific vulnerabilities, aiding in devising mitigation plans. |
In the CPES section the user can view in detail about the different CVEs that are identified for each CPE. The user can choose between different CPES by clicking on the drop down given on the top left of this section.
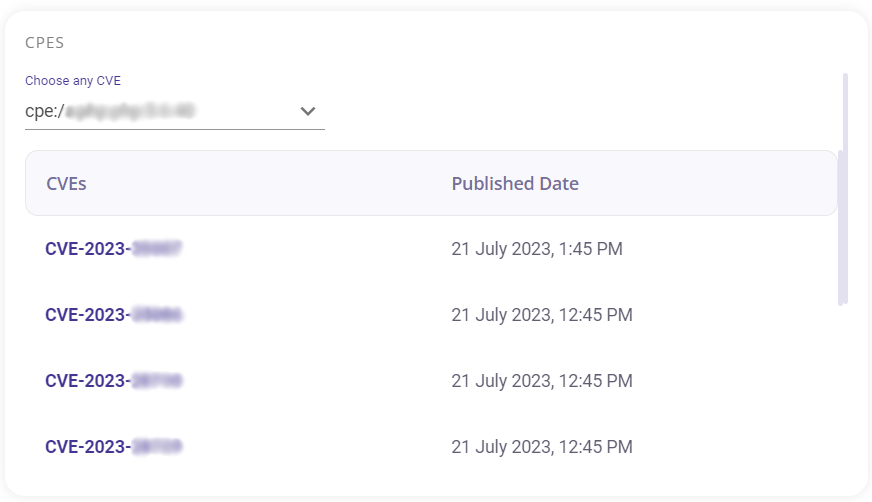
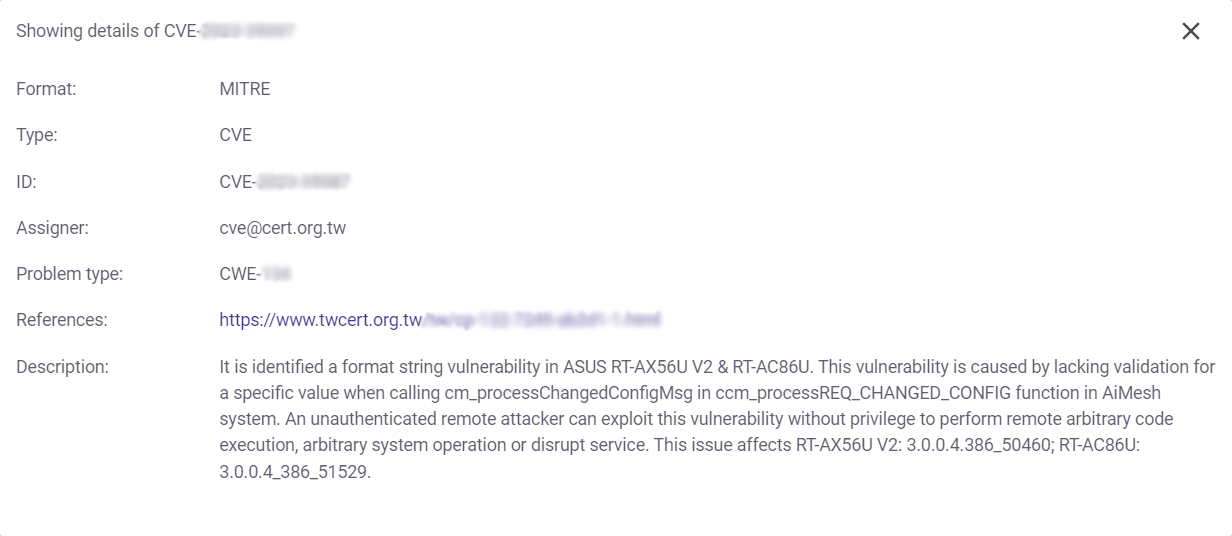
Clicking on a particular CVE provides more details about it.
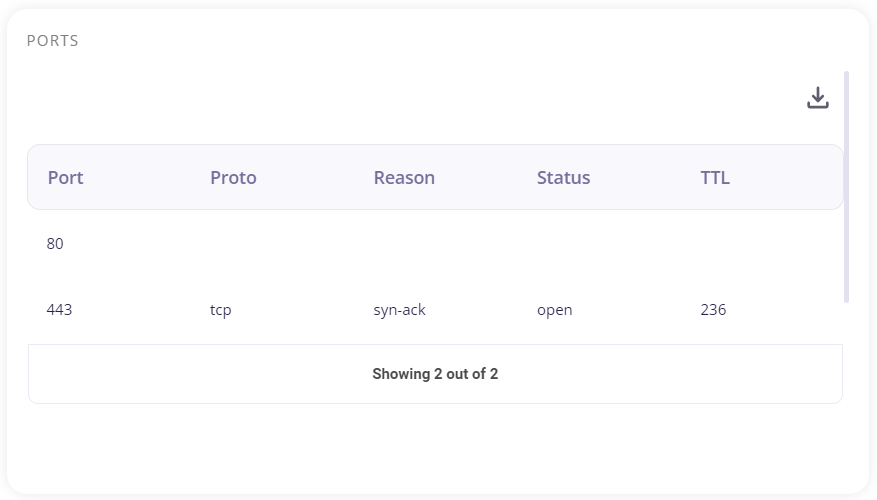
The ports section shows the ports which are open and the protocols they follow.
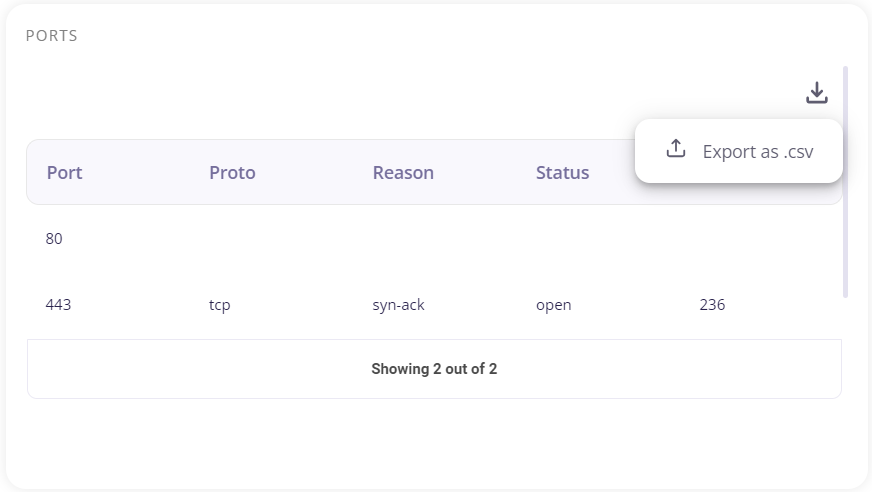
The list of open ports can be downloaded as .csv file by clicking on the download icon on the top right of this section.
The tags section marks the tags which would connect with the CVEs listed for this IP.
The hostnames section contains the name(s) of the host(s) from which the IP address was found.
The IP section gives the IP address whose details are listed here.
The possible CVEs indicates which CVEs can possibly be exploited.