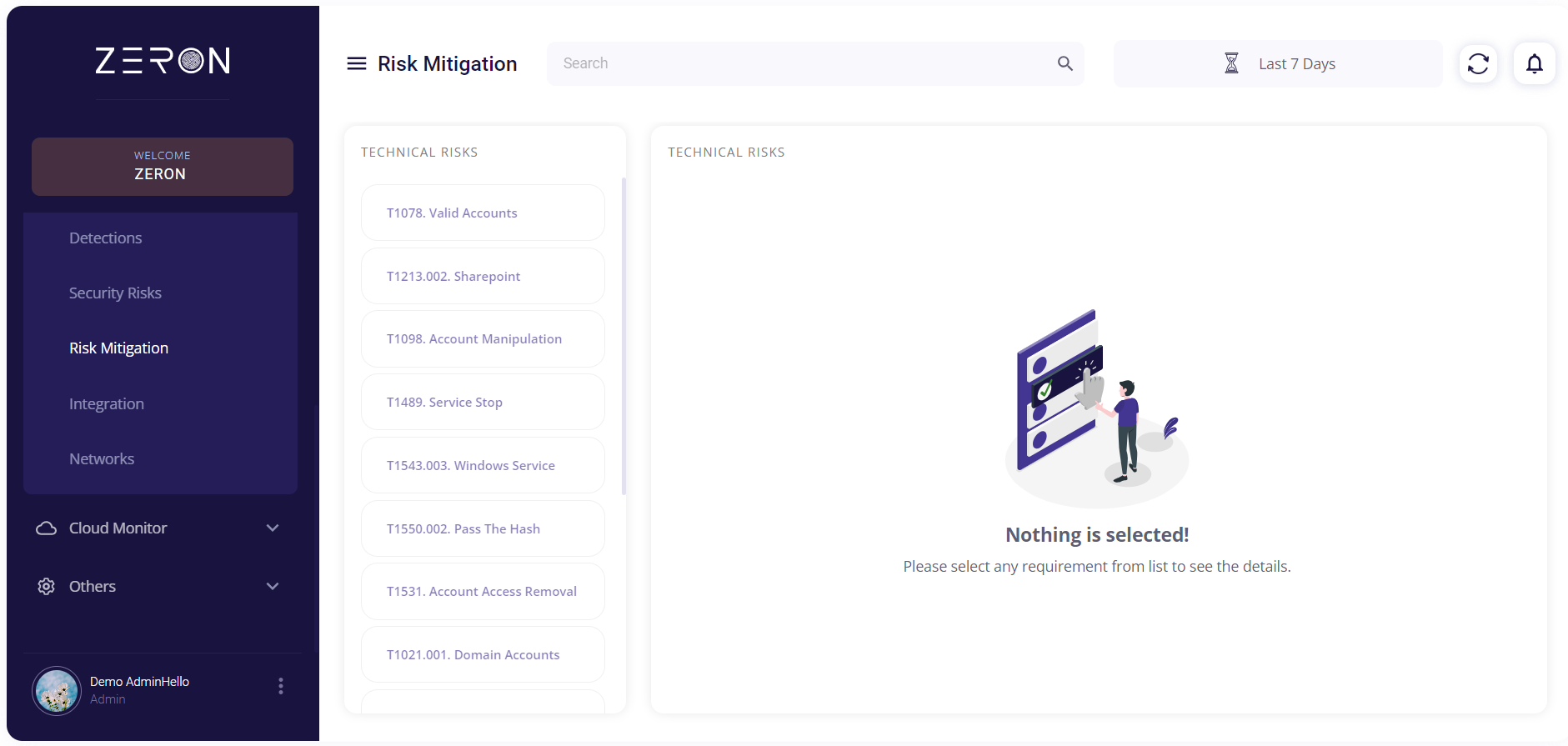
Risk Mitigation
This page contains information about the Mitre Att&ck tactics and enlists the technical risks that have been detected from them for the chosen period of time.
The default time period is always 2 hours. This can be changed in the time and date selection section of the navigation bar. For more info regarding time and date selection, click here.

On the left side, there is a list of technical risks. Clicking on a particular risk will provide the following details about that technical risk:
- Description
- An event count evolution graph
- Cybersecurity initiatives related to that technical risk
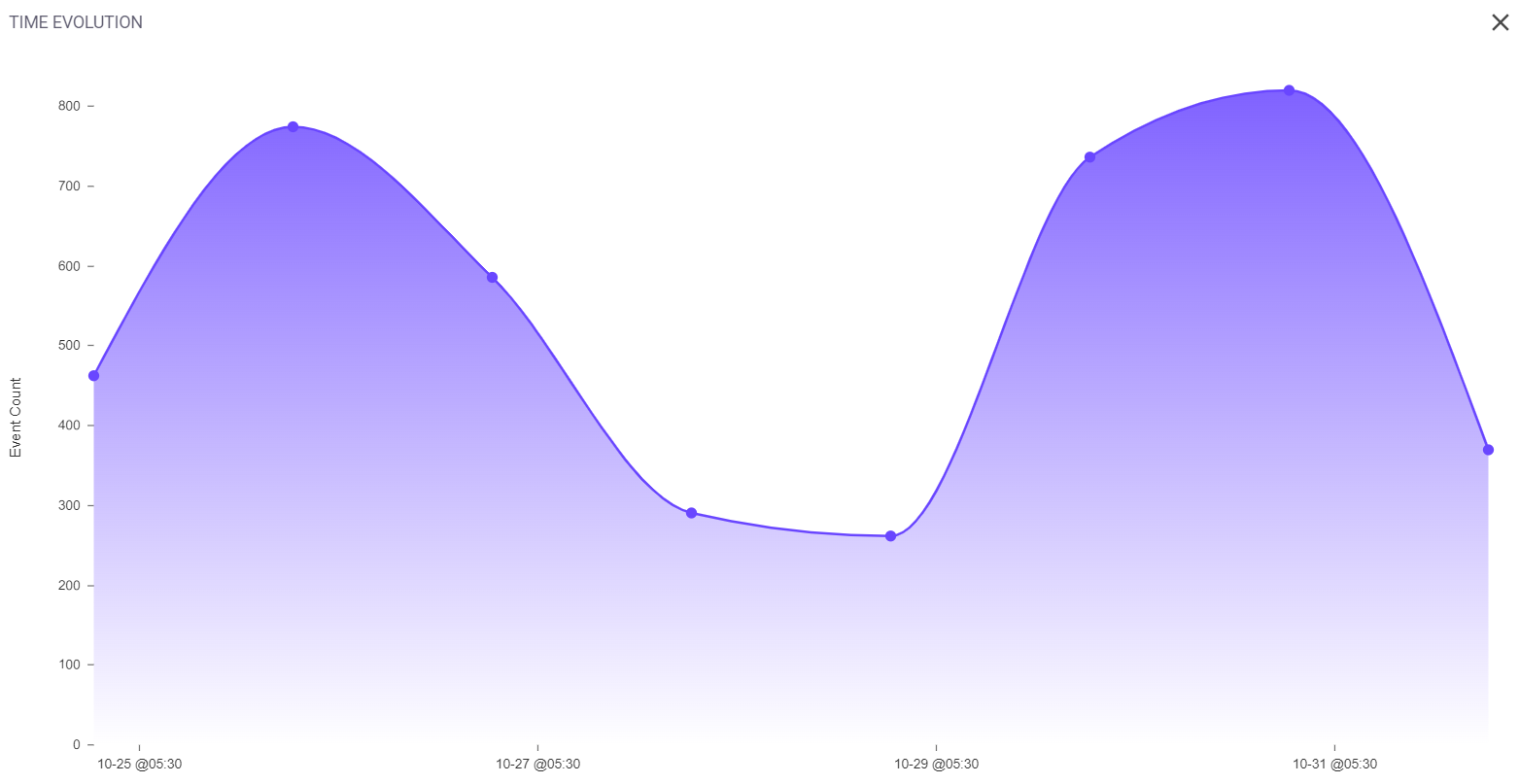
The event count evolution graph is produced by marking the event count at different time intervals. Hovering over a particular area will show the timestamp and number of events that have occurred at that time.
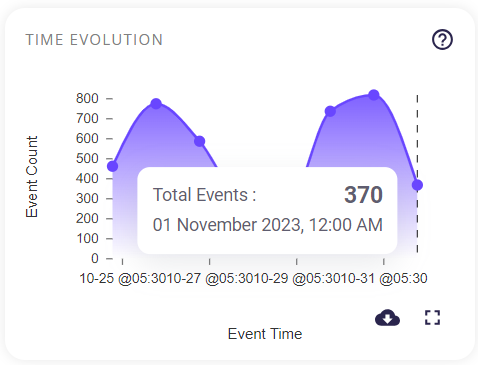
Clicking on the full-screen icon on the bottom right of this block provides the user with an enlarged view of the same graph. Similar to the preview, hovering over a particular area will show the timestamp and number of events that have occurred at that time.
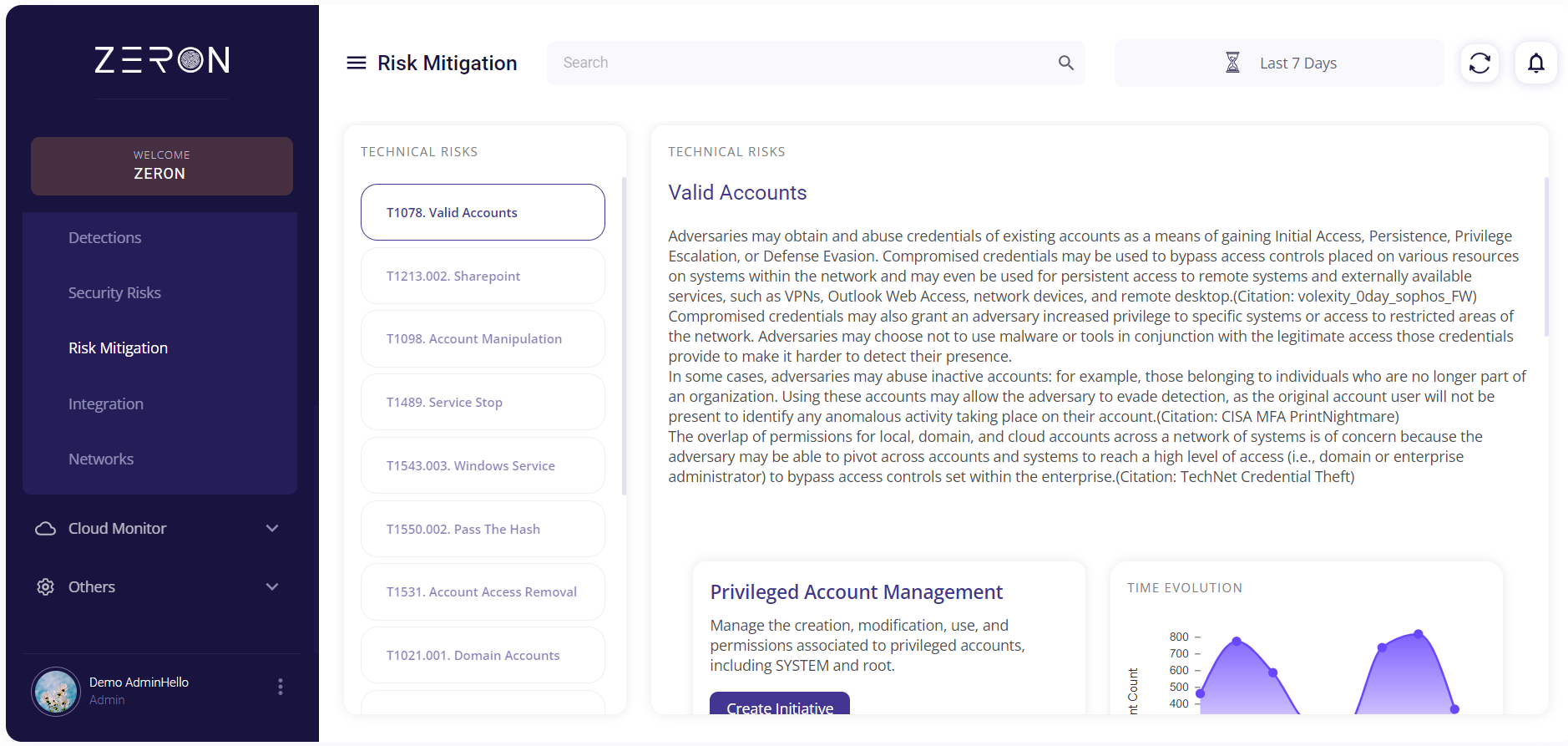
The cybersecurity initiatives that are related to that particular risk are given for each technical risk. The user can also create the required cybersecurity initiatives using the prompt given.
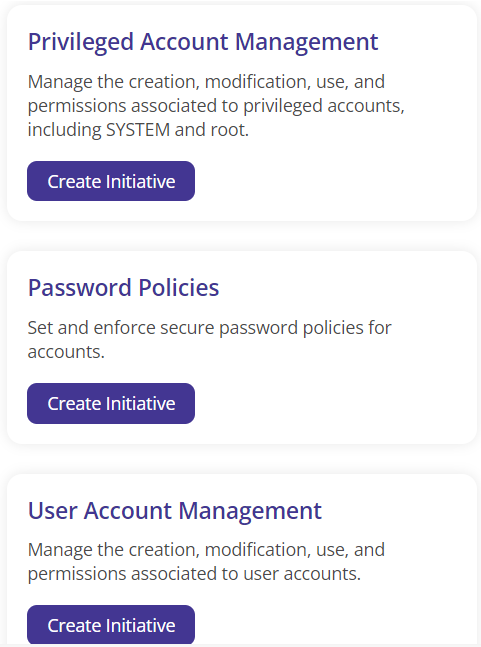
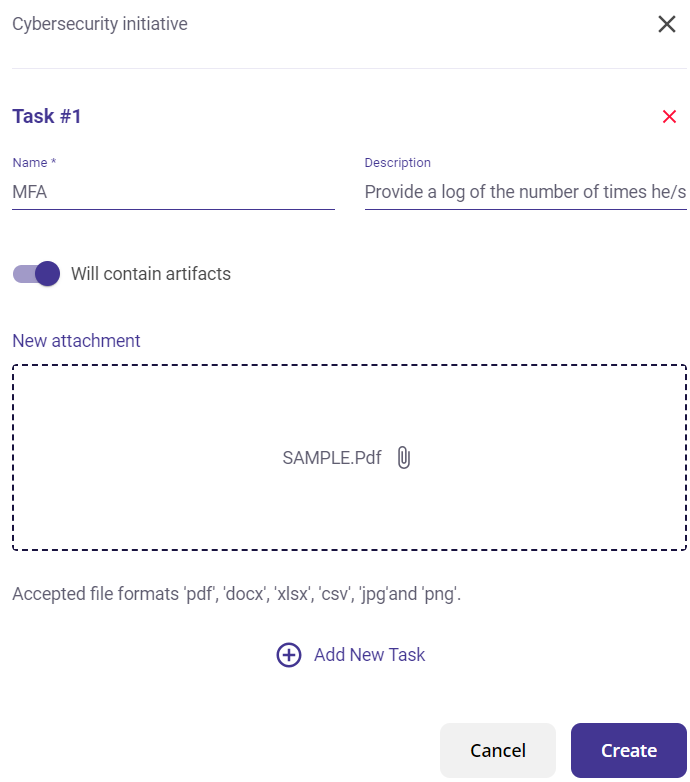
Steps to create a Cybersecurity initiative:
- Click on 'Create Initiative' to get the form.
- Fill in the name, description, date, and periodicity of the cybersecurity initiative.
- Allocate an assignee.
- Click on 'Create' to successfully create the initiative.
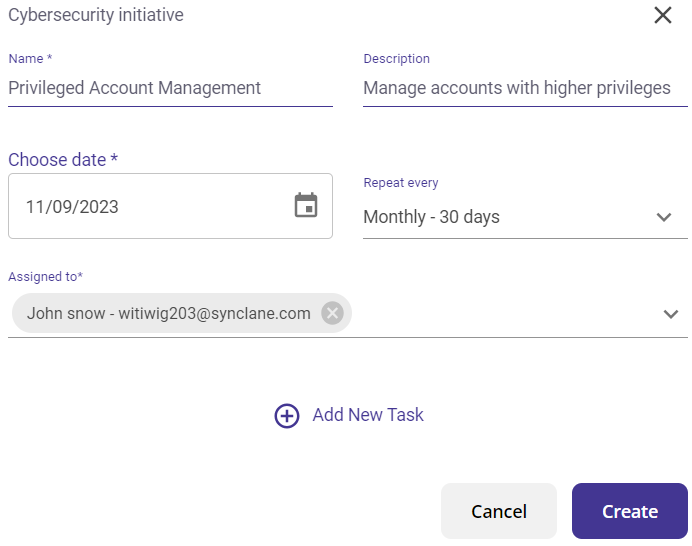
You may also choose to add a task by clicking on the 'Add New Task' button and filling in the name and description (and adding the attachment if required).